
Accurately Understand the Impact of Malware Infections on Your Systems
With MUSHIKAGO, organizations can safely conduct penetration tests that assume a malware infection scenario by using simulated malware designed to closely replicate the behavior of real malware.
This simulated malware faithfully mimics attackers’ post-compromise activities, reproducing a wide range of behaviors typically observed in the early stages of an intrusion, including:
・Internal reconnaissance
・Privilege escalation
・Lateral movement within the network
・Information collection
What MUSHIKAGO Can Do
Safe-by-Design Testing with No Impact on the Environment
Using real malware carries risks such as operational disruption and data corruption.
MUSHIKAGO’s simulated malware, however, is designed to have no impact on the environment, allowing organizations to safely and accurately validate:
How far a compromise could potentially spread
Which devices or configurations are most vulnerable to attack
At which stage endpoint detection and response (EDR) solutions detect malicious activity
These factors can be verified in advance without risking business operations.
As a result, organizations can visualize “what would happen if malware were to breach the environment” before an actual attack occurs, identify weaknesses, and prioritize effective countermeasures.
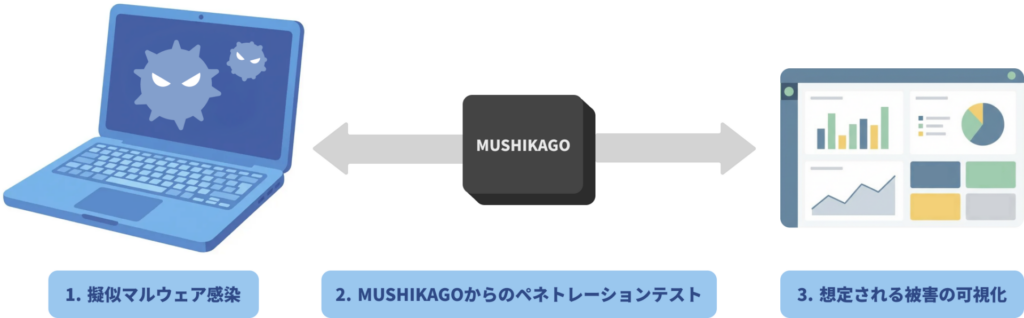
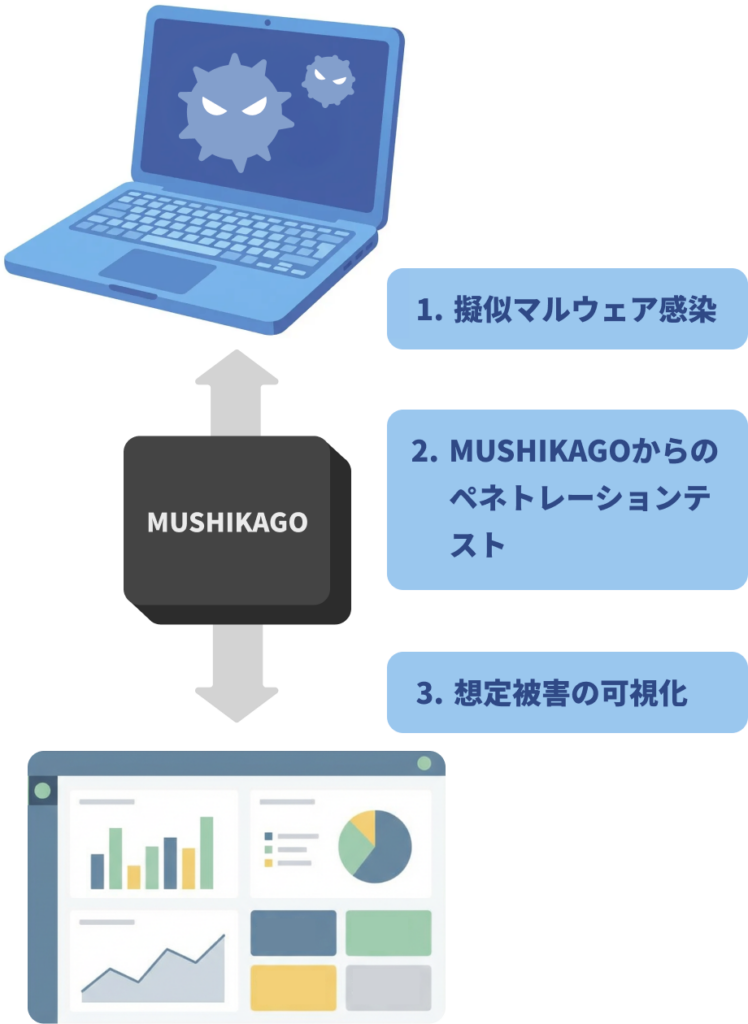
Continuous Improvement Based on the Latest Malware Trends
MUSHIKAGO's development team continuously researches the latest malware trends and incorporates their characteristics and behaviors into the simulated malware, refining it on an ongoing basis.
This enables the safe reproduction of scenarios that closely resemble real-world attacks, ensuring that validations are always based on current, real-world threats.
In addition, the simulated malware can be customized according to customer requirements.


Inquiries About the Service
Feel free to contact us with any questions about the service.
