
Support Case Studies
We deeply engage with our clients’ challenges and pain points—proposing the optimal solutions, managing every step of implementation, and enforcing robust security measures—providing end-to-end support until results are delivered.
Case1. Major Supermarket Chain
Challenges
・Unable to inventory endpoints or track vulnerabilities across locations, so security risks were unclear.
After MUSHIKAGO
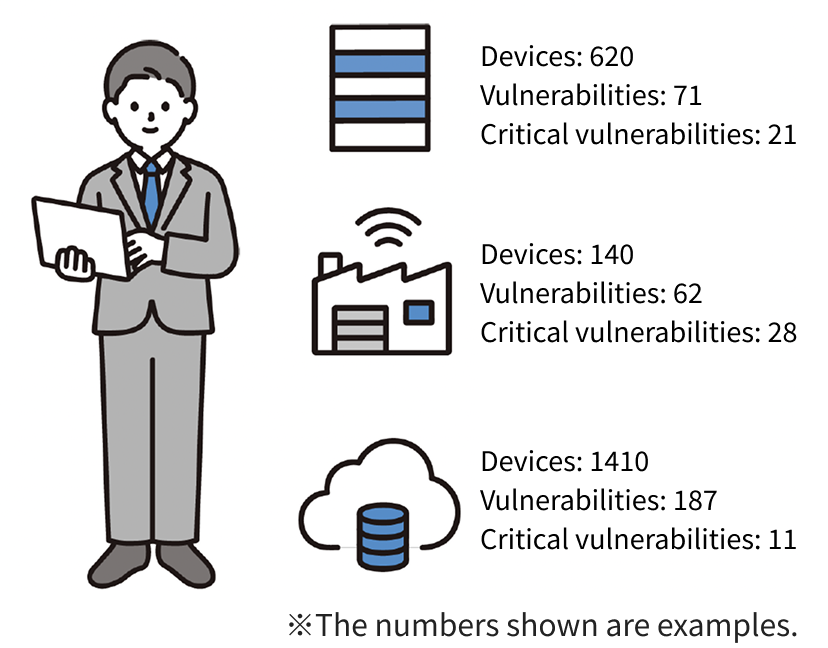
・Using MUSHIKAGO, they can now visualize all devices per location and instantly see endpoint counts, vulnerability counts, and any critical security risks.
Case2. Fintech Company
Challenges
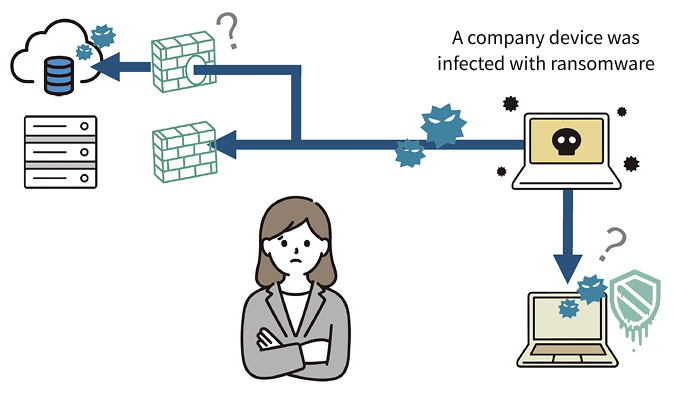
・Unsure whether company's internal security controls and configurations were working effectively.
・Wanted visibility into the potential impact of a ransomware infection.
After MUSHIKAGO
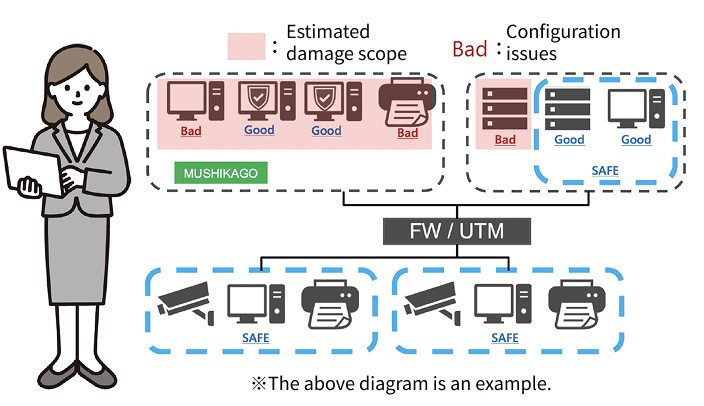
・A penetration test via MUSHIKAGO validated the effectiveness of the company's controls and uncovered any misconfigurations.
・By testing in an environment identical to their corporate PCs, the company gained a clear picture of the potential damage radius in the event of a ransomware outbreak.
Case 3. Automotive Parts Manufacturer
Challenges
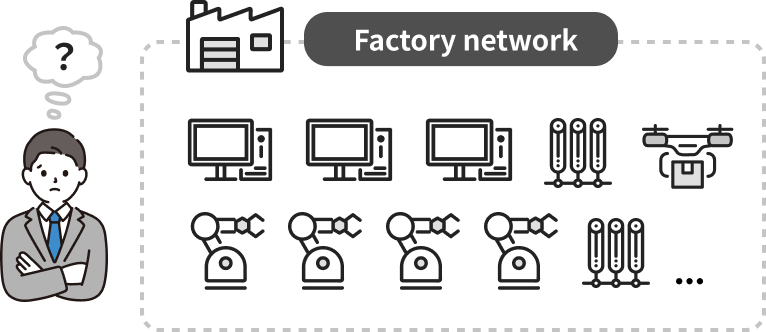
・No visibility into what was connected on the factory floor network.
・Received generic security recommendations for the factory network but lacked clarity on current risk levels and the minimal set of controls needed.
After MUSHIKAGO
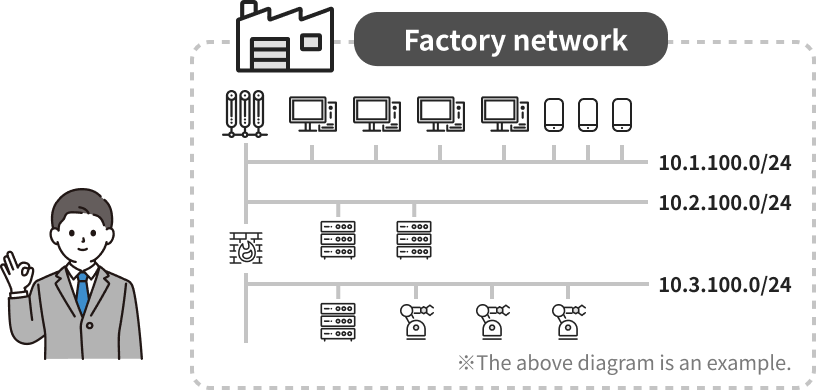
・MUSHIKAGO mapped out all endpoints and IP schemes on the factory network, enabling proper asset management.
・They now have an accurate inventory of their network state and a clear roadmap of necessary security measures and configurations.
Case 4. Railway Industry IT Subsidiary
Challenges
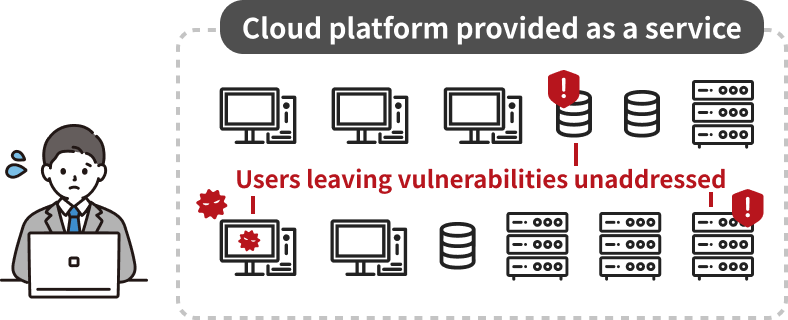
・Couldn’t determine how many machines in the company's cloud platform had unpatched vulnerabilities.
・With patching requirements expanding to internal servers, the company wanted to offer customers a service that reports vulnerability status on an ongoing basis.
After MUSHIKAGO
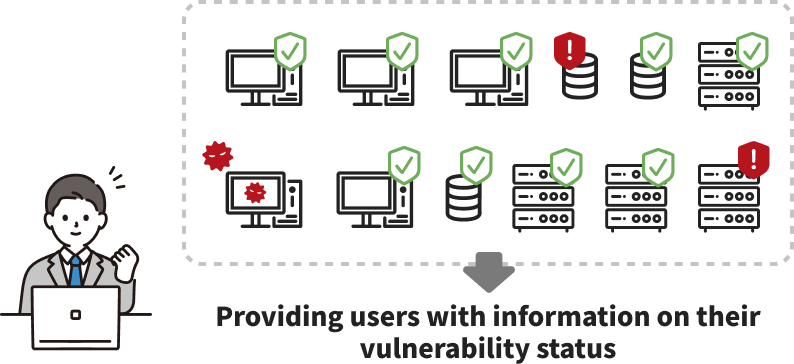
・By running regular vulnerability scans with MUSHIKAGO, the company now knows exactly how many machines have outstanding vulnerabilities and the severity of each.
主要な支援先企業様








