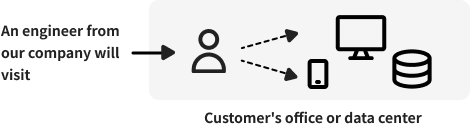
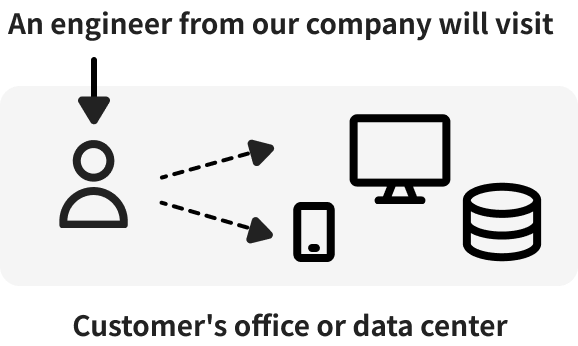
Penetration testing—formerly manual, now fully AI-automated.
Start in 2 weeks, Easy setup.
MUSHIKAGO
Penetration Testing Service
Already had a penetration test with another provider?
Try our service from ¥100,000 (tax included)!
※Offer valid for a 30-day period; other terms and conditions apply. Please contact us for details.
Concerned about cybersecurity?
Unsure where to deploy security solutions?
Already deployed but unsure if they are working properly?
Want to run a penetration test, but concerned about the time, effort*1, and cost*2?
*1: Manual tests require 2 experts and 3–6 months
2: Costs can exceed JPY 5 million per test (USD 30,000+)
Already using manual pen testing, but results depend too heavily on individual expertise.
Want to secure industrial systems, but lack access to qualified experts?


Let MUSHIKAGO Penetration Testing
solve these problems
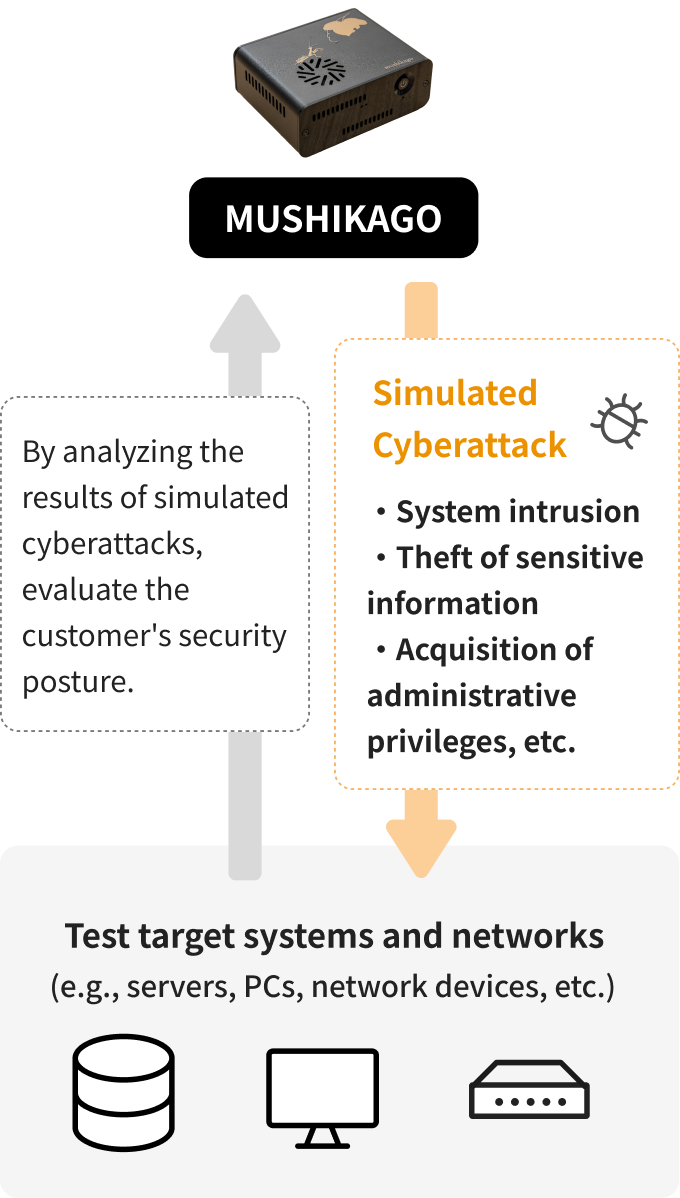
What Is the MUSHIKAGO Penetration Testing Service?
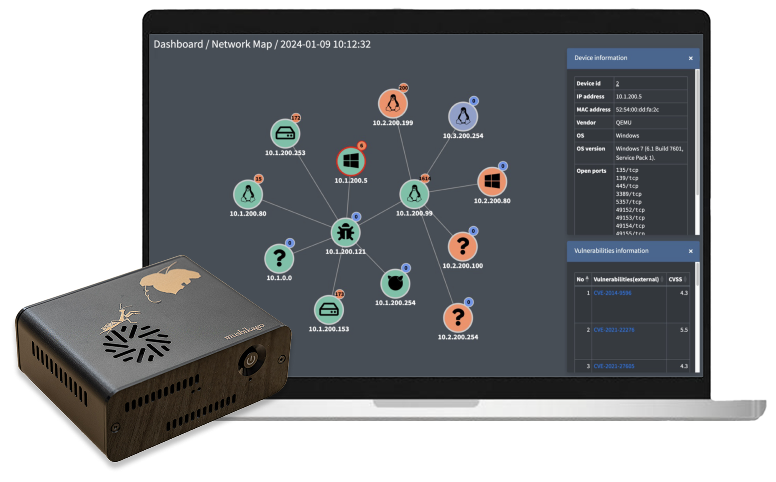
This service centers around our proprietary automated penetration testing device, MUSHIKAGO.
MUSHIKAGO simulates cyberattacks on your systems and networks to determine if test objectives (e.g., intrusion, data exfiltration, admin privilege takeover) can be achieved. This helps evaluate the effectiveness of your current security measures.
You can begin testing shortly after applying, making professional-grade penetration testing easy and accessible.

Clear Visibility Into Security Readiness
By using the MUSHIKAGO Penetration Testing Service, organizations can clearly assess the effectiveness of their internal security measures and frameworks.
Since each client's systems, network scopes, scenarios, and reporting needs differ, we tailor the testing plan through detailed consultations.
If necessary, we also offer manual penetration testing by experts for deeper analysis of risks found by MUSHIKAGO.
Contact Us or Download Our Brochure

Case Studies
Case 1. Major Supermarket Chain
Problem
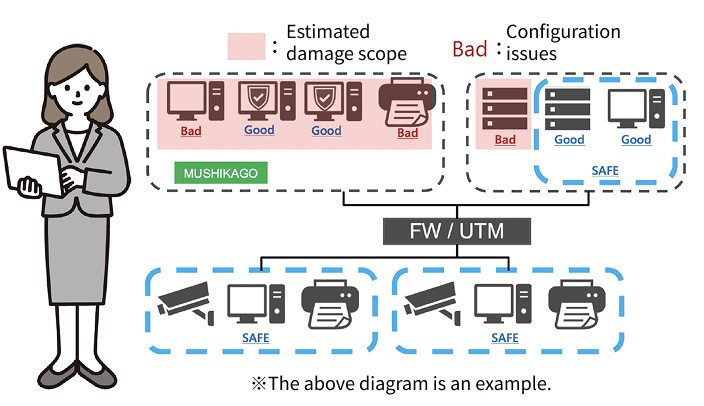
Head office, branches, and cloud environments—no unified view of device counts or vulnerability status.
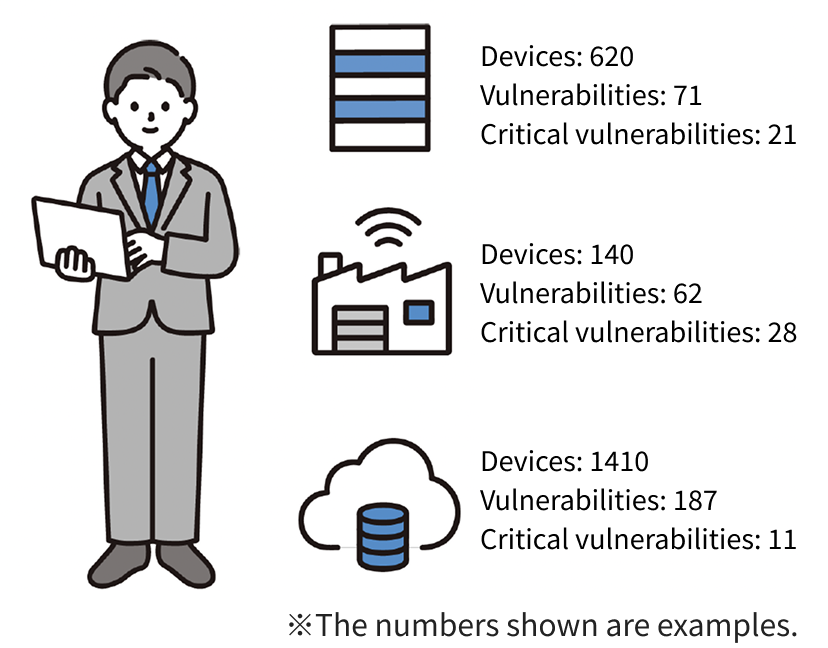
After MUSHIKAGO
MUSHIKAGO provided visibility across all sites, showing the number of devices, vulnerabilities, and critical security risks.
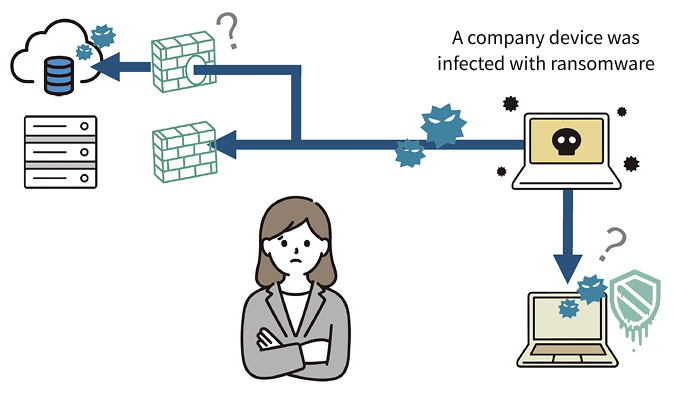
Case 2. Fintech Company
Problem
・Unsure if existing security settings are functioning properly.
・Wanted to understand the potential scope of a ransomware outbreak.
After MUSHIKAGO
・Gained clarity on misconfigurations and security control effectiveness.
・Tested in the same network environment as internal PCs, enabling accurate assessment of ransomware infection impact.
Contact Us or Download Our Brochure

Testing Methods
Choose from remote testing, on-site testing, or a hybrid approach based on your preferences.
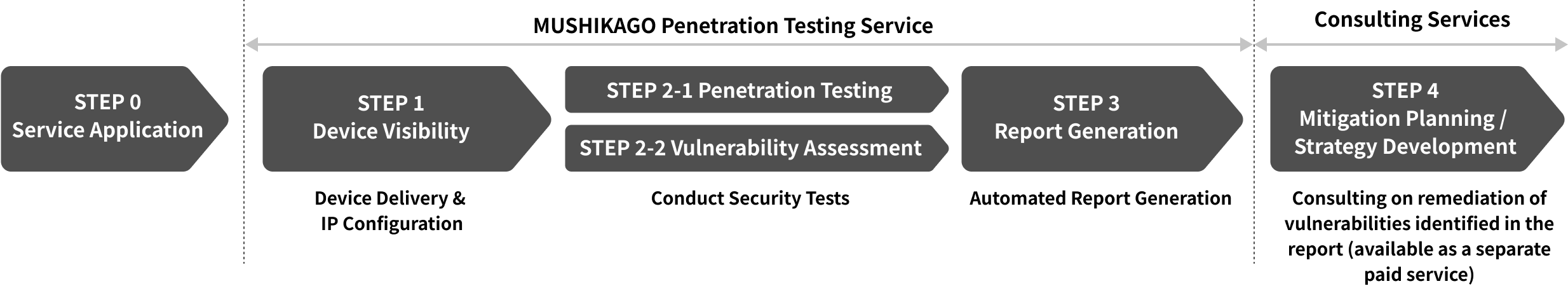
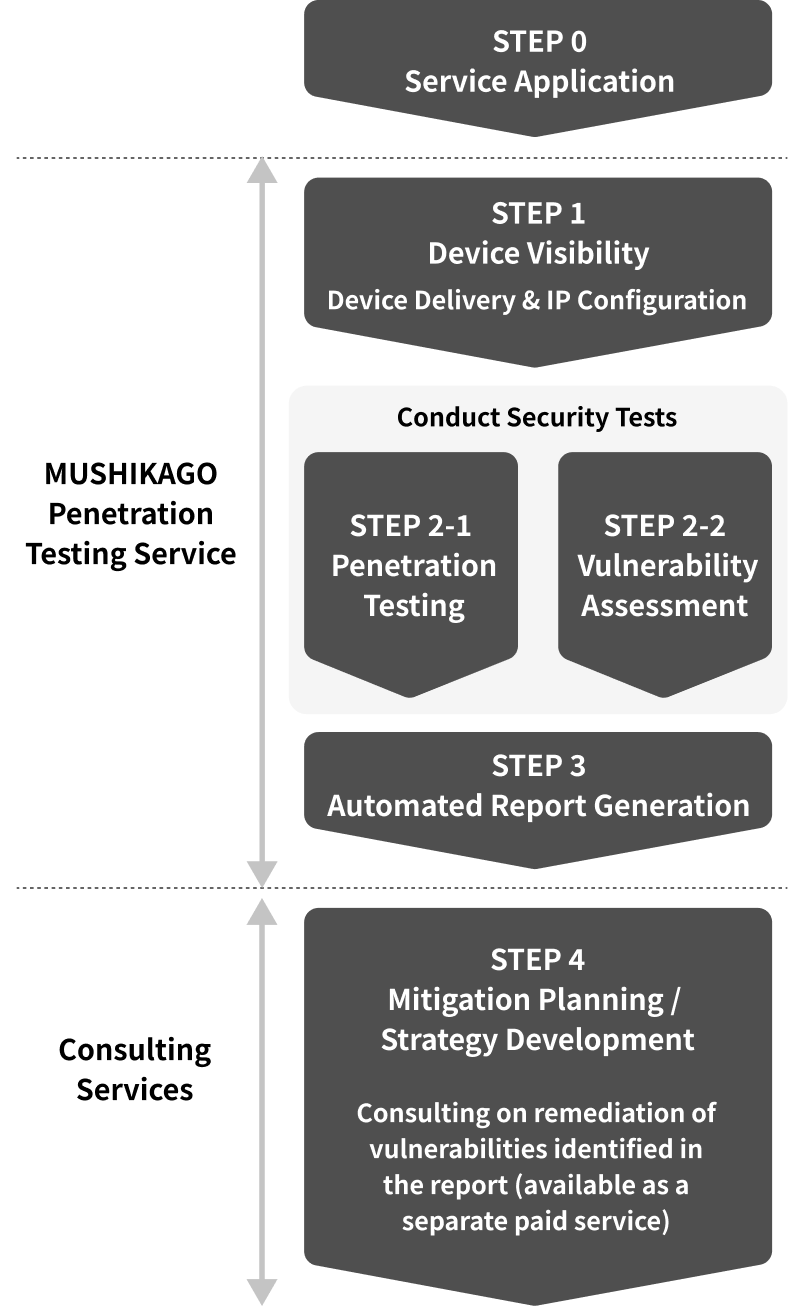
Service Flow

Contact Us or Download Our Brochure

Sample Test Items
This penetration testing service is based on internationally recognized penetration testing standards, including NIST 800-115 and PTES (Penetration Testing Execution Standard). Additionally, the test covers the latest security risks to ensure comprehensive security assessments.
The following table provides an example of test items when MUSHIKAGO is deployed within the target network to conduct penetration testing on various systems.
Information Gathering on the Target Systems
| Test Item | Description |
| ARP Scan | Uses ARP requests to identify and enumerate devices present within the target network and among the devices under test. |
| ICMP Scan | Utilize ICMP echo requests to confirm the existence of the target system. |
| TCP Scan | Conduct scans on TCP ports to identify open TCP ports on the target system. |
| UDP Scan | Conduct scans on UDP ports to identify open UDP ports on the target system. |
| OS and Version Detection | Analyze scan results to identify the operating system and its version on the target system. |
| Detection of Running Services and Version Identification | Analyze scan results to identify the exposed services and their respective versions. |
| FQDN and Domain Investigation | Investigate the Fully Qualified Domain Name (FQDN) and domain of the target system to confirm server and network information being used by the system. |
| Vulnerability Detection | Identify vulnerabilities based on the detected OS and service versions. Prioritize vulnerabilities that can be exploited for initial access or other purposes. |
| Exploration of Various Services | Test services like HTTP/HTTPS, SMB, SNMP, FTP, Telnet, SSH, RDP, and various databases by attempting logins using default credentials or password lists to confirm if credentials can be obtained. |
| Passive Scanning for Information Gathering | By deploying MUSHIKAGO on a mirror port, it analyzes communication traffic without affecting the network, collecting information about the target network and systems. |
Initial Intrusion into Target System
| Test Item | Description |
| Remote Login Service Login Attempts | If services such as Telnet, SSH, RDP, or WinRM are available, use valid credentials to test login. |
| Exploit Code Execution | If publicly available exploit codes are applicable, execute them to establish reverse shells or test for arbitrary operations. |
Information Gathering Post-Initial Intrusion
| Test Item | Description |
| Search for Sensitive Information | Collect sensitive information such as account details stored within the system. |
| User Enumeration | Obtain a list of local users and, if applicable, Active Directory (AD) users. |
| Sensitive Information Search in AD Environments | Use techniques such as AS-REP Roasting, Kerberoasting, Silver/Golden Ticket, and DCsync to check if authentication information for AD users can be obtained. |
| Malware Protection Software Investigation | Obtain lists of running processes and files to verify the presence of endpoint protection platforms (EPP) or endpoint detection and response (EDR) solutions. |
| Local Vulnerability Scanning | Analyze patch information, installed packages, and program details to detect known vulnerabilities. Identify vulnerabilities that could be used for privilege escalation. |
| Sniffing and Communication Analysis | Capture communication data on the compromised device to identify the protocols used and analyze communication details. |
| Search for Usable Software | Identify software such as remote login tools or password managers that could be leveraged for privilege escalation or lateral movement. |
Privilege Escalation
| Test Item | Description |
| Using Vulnerabilities for Privilege Escalation | If vulnerabilities suitable for privilege escalation are detected during local vulnerability scans, test if escalation can be achieved using exploit codes. |
| Using Misconfigurations for Privilege Escalation | Test if processes running with administrative privileges can be edited or operated by standard users, or if commands executable by administrators can be run by standard users to escalate privileges. |
| Using Credentials for Privilege Escalation | Test if administrative credentials (passwords or hashes) obtained can be used for privilege escalation. |
Post-Privilege Escalation Information Gathering
| Test Item | Description |
| Search for Sensitive Information | Investigate the extended range of access granted by administrative privileges to confirm if sensitive information inaccessible to standard users can be obtained. |
| Search for Authentication Credentials | Access processes or memory storing authentication credentials to test if such credentials can be obtained. |
Lateral Movement to Other Systems
| Test Item | Description |
| Port Scanning on Other Devices | Conduct TCP/UDP port scans on other devices to identify services running on those systems. |
| Using Vulnerabilities for Lateral Movement | Exploit vulnerabilities on other devices to establish reverse shells or perform arbitrary operations. |
| Using Credentials for Lateral Movement | Use obtained credentials to attempt login to other systems. |
Report
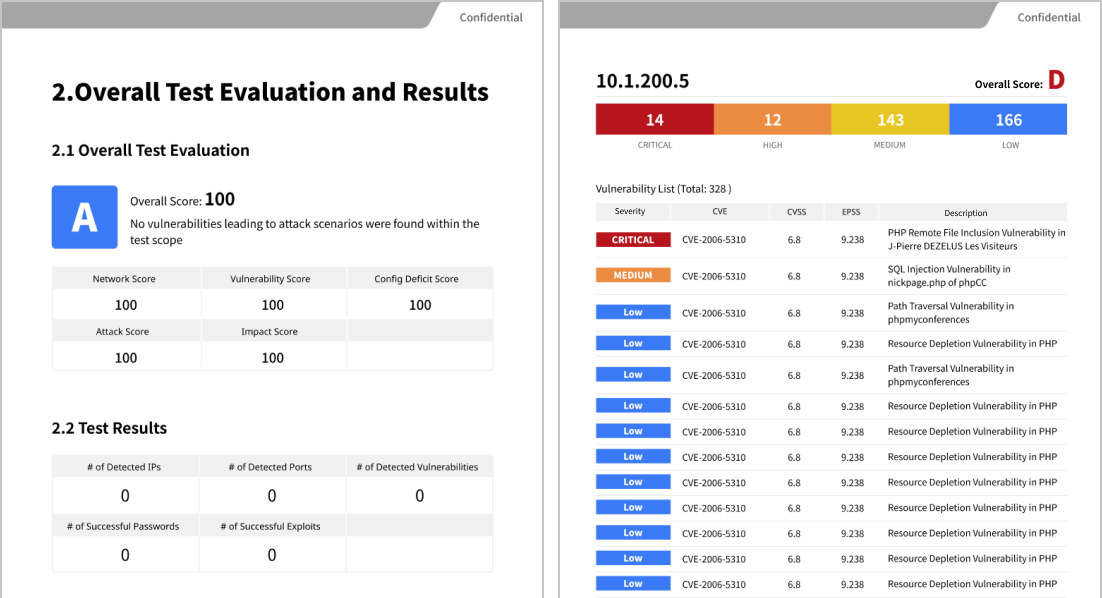
The test results are presented in an easy-to-understand format for clients, utilizing frameworks such as MITRE ATT&CK. They also comply with international penetration testing standards, including NIST 800-115 and PTES (Penetration Testing Execution Standard).
The report primarily consists of the following sections:
Recommended Remediation Measures, Executive Summary, Detailed Findings
Contact Us or Download Our Brochure
FAQ
What is Penetration Testing?
…Penetration Testing, also known as "pen testing," is a type of security assessment that simulates cyberattacks conducted by hackers to identify vulnerabilities within IT systems. It helps visualize security risks in devices, networks, web applications, and cloud environments, and assesses how deeply an attacker could penetrate and what kind of damage they could inflict. Based on the test results, companies can strengthen their defenses and prevent future cyberattacks.
What Are the Advantages of AI-Driven Penetration Testing?
…Traditional penetration testing is performed manually by security experts (Red Teams), which requires substantial time, cost, and resources. The results are often dependent on individual skills and cover only selected systems. As a result, comprehensive coverage is rare.
Our AI-driven approach simulates attacker behavior like a Red Team, using up-to-date attack techniques to conduct wide-ranging automated tests. This enables cost reduction, shorter execution times, and improved security posture.
Given that attackers are increasingly using AI in their methods, relying solely on manual testing is no longer sufficient. If you're seeking to minimize cyber risk, we highly recommend considering our AI-powered device, MUSHIKAGO.
What is a Vulnerability Assessment?
…A vulnerability assessment is a test that identifies and evaluates security flaws in systems, applications, and networks. Its goal is to prevent breaches and data leaks by proactively identifying potential risks in servers, network devices, PCs, and more.
MUSHIKAGO makes it easy to gain visibility into network-connected devices, their versions, patch status, and known vulnerabilities. This helps organizations manage and reduce their overall security risks.
Which Industries and Organizations Benefit from Penetration Testing and Vulnerability Assessments?
…All organizations benefit from understanding and strengthening their cybersecurity posture. Our solutions are especially valuable in industries such as healthcare, manufacturing, e-commerce, and cloud services.
MUSHIKAGO is fully operable in offline environments, making it ideal for use in factories and other isolated networks.
How Long Does Deployment Take?
…After application, we deliver the device within a few business days to one week. Simply connect the device and configure the IP address—no software installation is required.
Is the Service Subscription-Based or One-Time Purchase?
…The service is offered on a subscription basis. If a one-time purchase is required, please contact us separately.
What Is the Contract Duration?
…You can use the service for as little as one month. Annual plans are also available. We tailor the number of devices and contract period based on your specific requirements.
How Reliable Is the MUSHIKAGO Product?
…MUSHIKAGO is a domestically developed product recognized by Japan's Ministry of Economy, Trade and Industry (METI). Our achievements include:
・Adopted by the Cabinet Office's Advanced Cybersecurity Program (2024)
・Presentations at Black Hat USA (2021, 2022)
・Selected for NEDO's NEP Program (2021)
What Languages Are Supported?
…All interfaces, reports, and manuals are available in Japanese and English. Please contact us for overseas deployment options.
Do You Provide Support for Post-Test Remediation?
…Upon request, we provide report briefings to help you understand the test results. For detailed technical advice and remediation planning, we offer a separate paid consulting service.
Other Services from Powder Keg Technologies

Security Health Check
A comprehensive assessment of your IT environment’s current security level.
> Learn More

Web Application Vulnerability Assessment
Identifies flaws in your operational websites and web apps.
> Learn More

Platform Vulnerability Assessment
Evaluates risks and configuration issues in servers, OS, middleware, and network infrastructure.
> Learn More
Contact Us or Download Our Brochure

Powder Keg Technologies
Recognized Achievements