MUSHIKAGO
Penetration Testing Service

About MUSHIKAGO Penetration Testing
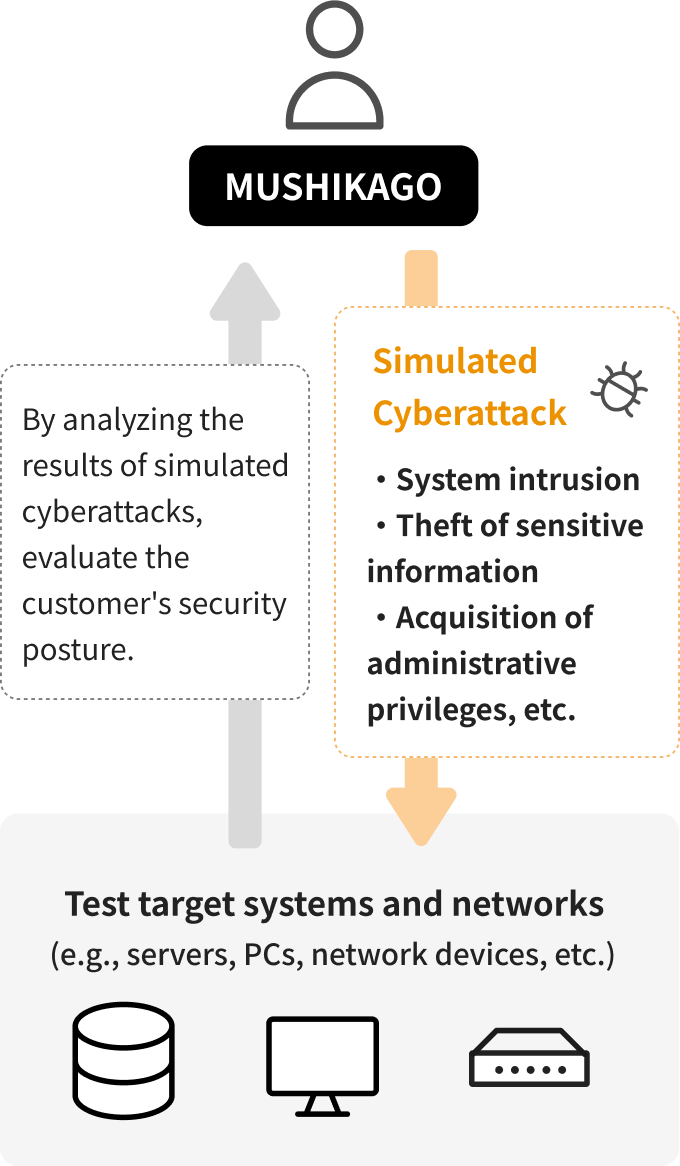
The MUSHIKAGO Penetration Testing Service is a service centered around penetration testing using MUSHIKAGO, an automated penetration testing device developed in-house by our company.
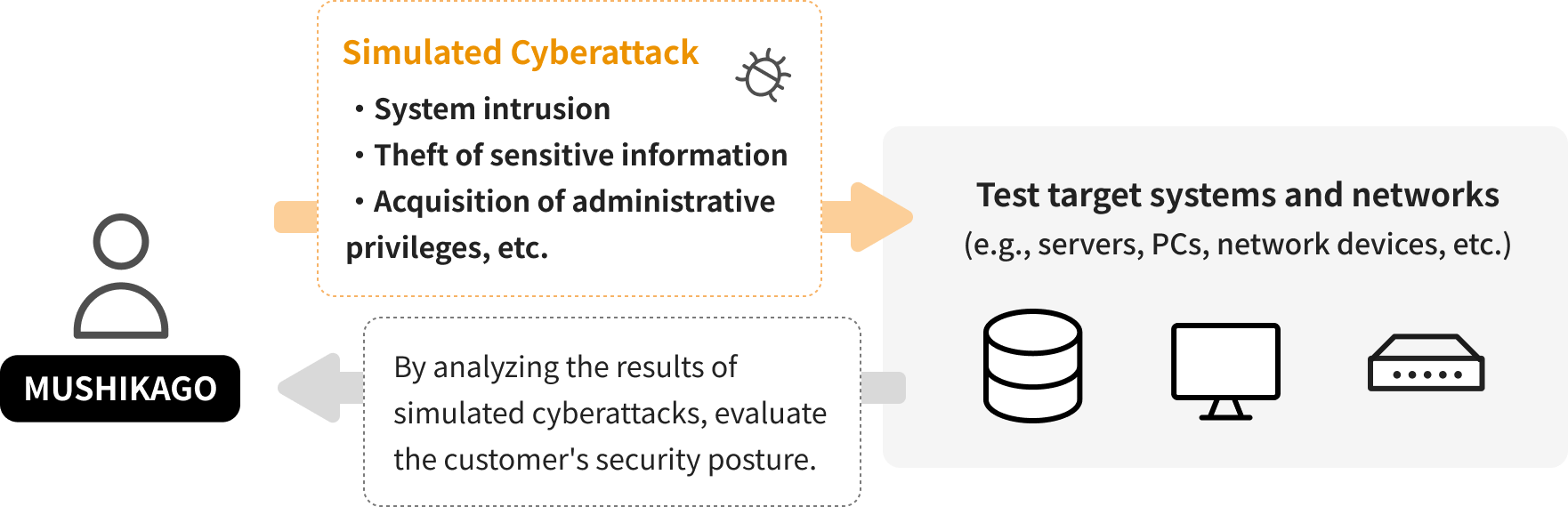
MUSHIKAGO conducts simulated cyberattacks on target systems and networks to verify whether test objectives—such as gaining unauthorized access, extracting sensitive information, and obtaining administrative privileges—can be achieved. This allows us to assess the effectiveness of your security measures.
With this service, penetration testing can begin within a short period after application, enabling easy and efficient security testing.
By using the MUSHIKAGO Penetration Testing Service, organizations can clearly evaluate the effectiveness of their security measures and incident response frameworks. Since test targets, network scope, attack scenarios, and reporting requirements vary by customer, we work closely with each client beforehand to tailor the test to their specific needs.
Additionally, for security risks identified through MUSHIKAGO Penetration Testing, we also offer a manual penetration testing service for a more detailed security assessment.

Our MUSHIKAGO penetration testing service is listed in the "Information Security Service Standards Compliant Service List" as a service that complies with the "Information Security Service Standards" established by the Ministry of Economy, Trade and Industry (METI) of Japan.
These standards were established by METI with the aim of identifying information security services that strive to maintain and improve a certain level of quality.
The compliance with these standards is confirmed through a review by the Japan Information Security Audit Association (JASA), a specified non-profit organization. It certifies that the service meets specific technical and quality management requirements, and demonstrates a commitment to maintaining and improving service quality.

Strengths of MUSHIKAGO Penetration Testing Service
Comprehensive Penetration Testing
・Since MUSHIKAGO is fully automated, it enables broad and thorough penetration testing.
Quick Testing Deployment
・As a MUSHIKAGO-driven penetration test, testing can begin in as little as two weeks.
Customizable Settings
・Developed in-house, MUSHIKAGO allows for custom configurations based on client needs.
Expert-Led Security Assessments
・Attacker’s Perspective: Conducted by Offensive Security-certified professionals and CTF international competition participants.
・User’s Perspective: Performed by security experts from major critical infrastructure sectors.
・Client-Focused Approach: Led by former consultants from top security firms who understand enterprise security needs.

Test Methodology
Clients can choose from the following two methods, or a hybrid approach, depending on their requirements:
Test Flow


Sample Test Items
This penetration testing service is based on internationally recognized penetration testing standards, including NIST 800-115 and PTES (Penetration Testing Execution Standard). Additionally, the test covers the latest security risks to ensure comprehensive security assessments.
The following table provides an example of test items when MUSHIKAGO is deployed within the target network to conduct penetration testing on various systems.
Information Gathering on the Target Systems
| Test Item | Description |
| ARP Scan | Uses ARP requests to identify and enumerate devices present within the target network and among the devices under test. |
| ICMP Scan | Utilize ICMP echo requests to confirm the existence of the target system. |
| TCP Scan | Conduct scans on TCP ports to identify open TCP ports on the target system. |
| UDP Scan | Conduct scans on UDP ports to identify open UDP ports on the target system. |
| OS and Version Detection | Analyze scan results to identify the operating system and its version on the target system. |
| Detection of Running Services and Version Identification | Analyze scan results to identify the exposed services and their respective versions. |
| FQDN and Domain Investigation | Investigate the Fully Qualified Domain Name (FQDN) and domain of the target system to confirm server and network information being used by the system. |
| Vulnerability Detection | Identify vulnerabilities based on the detected OS and service versions. Prioritize vulnerabilities that can be exploited for initial access or other purposes. |
| Exploration of Various Services | Test services like HTTP/HTTPS, SMB, SNMP, FTP, Telnet, SSH, RDP, and various databases by attempting logins using default credentials or password lists to confirm if credentials can be obtained. |
| Passive Scanning for Information Gathering | By deploying MUSHIKAGO on a mirror port, it analyzes communication traffic without affecting the network, collecting information about the target network and systems. |
Initial Intrusion into Target System
| Test Item | Description |
| Remote Login Service Login Attempts | If services such as Telnet, SSH, RDP, or WinRM are available, use valid credentials to test login. |
| Exploit Code Execution | If publicly available exploit codes are applicable, execute them to establish reverse shells or test for arbitrary operations. |
Information Gathering Post-Initial Intrusion
| Test Item | Description |
| Search for Sensitive Information | Collect sensitive information such as account details stored within the system. |
| User Enumeration | Obtain a list of local users and, if applicable, Active Directory (AD) users. |
| Sensitive Information Search in AD Environments | Use techniques such as AS-REP Roasting, Kerberoasting, Silver/Golden Ticket, DCsync, and AD CS (ESC attack) to check if authentication information for AD users can be obtained. |
| Malware Protection Software Investigation | Obtain lists of running processes and files to verify the presence of endpoint protection platforms (EPP) or endpoint detection and response (EDR) solutions. |
| Local Vulnerability Scanning | Analyze patch information, installed packages, and program details to detect known vulnerabilities. Identify vulnerabilities that could be used for privilege escalation. |
| Sniffing and Communication Analysis | Capture communication data on the compromised device to identify the protocols used and analyze communication details. |
| Search for Usable Software | Identify software such as remote login tools or password managers that could be leveraged for privilege escalation or lateral movement. |
Privilege Escalation
| Test Item | Description |
| Using Vulnerabilities for Privilege Escalation | If vulnerabilities suitable for privilege escalation are detected during local vulnerability scans, test if escalation can be achieved using exploit codes. |
| Using Misconfigurations for Privilege Escalation | Test if processes running with administrative privileges can be edited or operated by standard users, or if commands executable by administrators can be run by standard users to escalate privileges. |
| Using Credentials for Privilege Escalation | Test if administrative credentials (passwords or hashes) obtained can be used for privilege escalation. |
Post-Privilege Escalation Information Gathering
| Test Item | Description |
| Search for Sensitive Information | Investigate the extended range of access granted by administrative privileges to confirm if sensitive information inaccessible to standard users can be obtained. |
| Search for Authentication Credentials | Access processes or memory storing authentication credentials to test if such credentials can be obtained. |
Lateral Movement to Other Systems
| Test Item | Description |
| Port Scanning on Other Devices | Conduct TCP/UDP port scans on other devices to identify services running on those systems. |
| Using Vulnerabilities for Lateral Movement | Exploit vulnerabilities on other devices to establish reverse shells or perform arbitrary operations. |
| Using Credentials for Lateral Movement | Use obtained credentials to attempt login to other systems. |
Report
The test results are presented in an easy-to-understand format for clients, utilizing frameworks such as MITRE ATT&CK. They also comply with international penetration testing standards, including NIST 800-115 and PTES (Penetration Testing Execution Standard).
The report primarily consists of the following sections:
1. Recommended Remediation Measures: Suggestions for addressing identified vulnerabilities.
2. Executive Summary: A concise overview of the test results.
3. Detailed Findings: A comprehensive summary of the test results.

Tool Used in this Test
In our testing service, we leverage MUSHIKAGO, combining manual and automated testing methods to conduct assessments from all possible angles and perspectives:
Certifications and Expertise
Our engineers possess high skills and extensive experience, including certifications such as:
・Offsec Certifications (OSEP/OSCP/OSWE etc.)
・PortSwigger Certifications (BSCP, etc.)
・Information Security Management Specialist
Pricing
The cost of the penetration testing service varies depending on the specific test scenarios and requirements requested by the customer.
After a detailed consultation, we will provide a customized quote based on your testing needs.


Inquiries About the Service
Feel free to contact us with any questions about the service.